
Zimperium’s Mobile App Protection Suite
(MAPS) | Mobile App Security
A Platform Approach
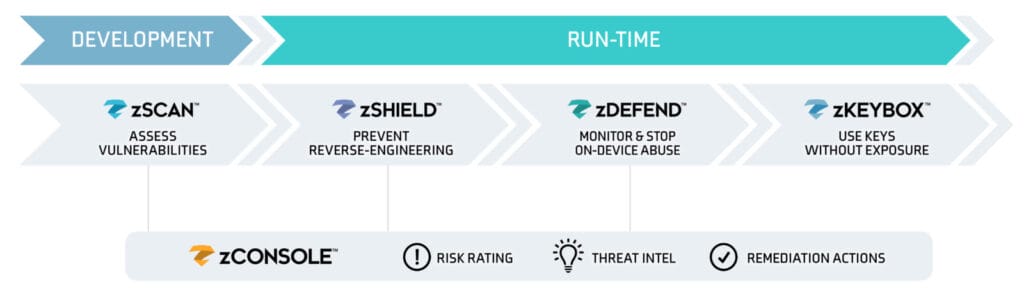
The Mobile Application Protection Suite (MAPS) from Zimperium provides four capabilities, including Mobile Application Security Testing (MAST), App Shielding, Key Protection, and Runtime Protection (RASP). The suite provides mobile app teams with centralized threat visibility and comprehensive in-app protection from development through runtime. It combines both inside-out and outside-in security approaches to help organizations build compliant, secure, and resilient mobile apps.
MAPS is a key component of the Zimperium Mobile-First Security Platform™ that secures mobile devices and mobile applications.
“With its comprehensive functional capabilities, compelling technology differentiation, and robust customer value proposition, Zimperium is well-positioned to maintain and grow its market share amongst mid-market to large enterprise segments.”
— Quadrant Knowledge Solutions’ SPARK Matrix™: In-App Protection, 2023
Key Capabilities

Mobile Application
Security Testing
Discover and fix compliance, privacy, and security issues within the development process before you publicly release your app binaries.

Application
Shielding
Harden and protect your app with advanced obfuscation and anti-tampering functionality to protect the source code, intellectual property (IP), and data within the application.

Runtime Visibility
& Protection
Enable the mobile application to detect and protect itself by taking actions on end user devices, even without network connectivity.

Cryptographic
Key Protection
Protect confidential data by securing cryptographic keys with white-box cryptography so they cannot be discovered, extracted, or manipulated.

Mobile Application
Security Testing
Discover and fix compliance, privacy, and security issues within the development process before you publicly release your app binaries.

Application
Shielding
Harden and protect your app with advanced obfuscation and anti-tampering functionality to protect the source code, intellectual property (IP), and data within the application.

Runtime Visibility
& Protection
Enable the mobile application to detect and protect itself by taking actions on end user devices, even without network connectivity.

Cryptographic
Key Protection
Protect confidential data by securing cryptographic keys with white-box cryptography so they cannot be discovered, extracted, or manipulated.
Trusted Mobile Application Security Solution Across Industries










Key AppSec Outcomes

Develop secure apps faster

Minimize exploitable vulnerabilities

Comply with standards & regulations

Make apps tamper resistant

Make apps self-defending

Update security dynamically, over the air (OTA)
“Modern application architectures such as mobile move software logic to the front end, and place sensitive data on the devices. These architectures expose functionality that, unless shielded, can lead to attacks such as data leakage on the app or its back end, and fraudulent use or compromise of the user’s device application functionality.”
— Gartner’s “Application Security Hype Cycle 2023” Report
(Published 24 July 2023; Dionisio Zumerle)
Why Zimperium MAPS

Centralized Threat &
Risk Visibility

Comprehensive Pre-Release
& Post-Release Protection

Internal &
External Compliance

Optimized For
Size and Performance
Over-The-Air
Security Updates

Privacy-First
Design
“We needed to rebuild and relaunch our apps quickly and efficiently. MAPS provided a one-stop-shop approach to identifying security, privacy, and compliance risks during app development and protecting/monitoring apps from attacks while in use. As impressive, Zimperium’s knowledge, responsiveness, and genuine care are exceptional.”
— SVP of Application Development, North American Banking Company












